There is an unwritten rule in the IT security industry which says that “the more widespread a solution is, the more likely it is to be targeted” (that is, the more exposed it is to security threats). This applies to any software, be it commercial or open source, regardless of its purpose.
Fortunately, apart from disadvantages such as the increased security risk, this state of affairs also has some advantages. There are quite a few security professionals and experts who test software security features on their own and report issues to manufacturers or take part in bug bounty schemes. Under these schemes, manufacturers make their products available for security testing and pay a bounty for any reported and documented vulnerabilities.
In this article, you will find answers to the following questions:
- How is WordPress used commercially by businesses?
- Why can every WordPress instance available on the Internet be at risk?
- In what situations can an attack take place and who can execute it?
- How do you ensure the security of a blog built on WordPress and what considerations should you bear in mind?
- How can Onwelo help secure your corporate blog?
One of the solutions that enjoy great popularity and are subject to constant security testing by the community is WordPress, a CMS (Content Management System) platform distributed under an open GPLv2 license that permits both private and commercial use. WordPress’s main goal is to provide a tool for running a blog, but it can also be extended with additional functionality. This is possible due to the availability of a large number of free and paid plugins that enhance the platform’s capabilities. And as we continue to list the platform’s advantages, it is hard not to mention the support provided by a truly enormous community, which contributes to the platform’s rapid development.
Commercial use
The reason why I’m mentioning WordPress is that I have noticed a growing number of corporate blogs which use the platform for content management and delivery. The purpose of these blogs is to reach out to customers and promote the company’s brand and competencies.
Here at Onwelo, for example, we try to use our blog not only to showcase our core competencies, but also to share our knowledge.
WordPress can be more than just a blog: it can also act as a company’s one-page website, an artist’s portfolio or a dedicated page where product or service offerings are presented. Another example of a commercial use of WordPress is running a company’s core business process, a scenario that is particularly popular with different types of editorial teams or websites.
There are many possibilities for using WordPress in this manner, and we could probably come up with even more applications that can deliver a variety of business benefits.
Is WordPress a secure solution?
From a technical point of view, WordPress is a PHP application which must be run on an HTTP server and requires access to a database that stores all the information and content to be displayed on the site. Generally speaking, all these prerequisites can be met by a single server that is publicly available on the Internet at an address like www.blog.mycompany.com.
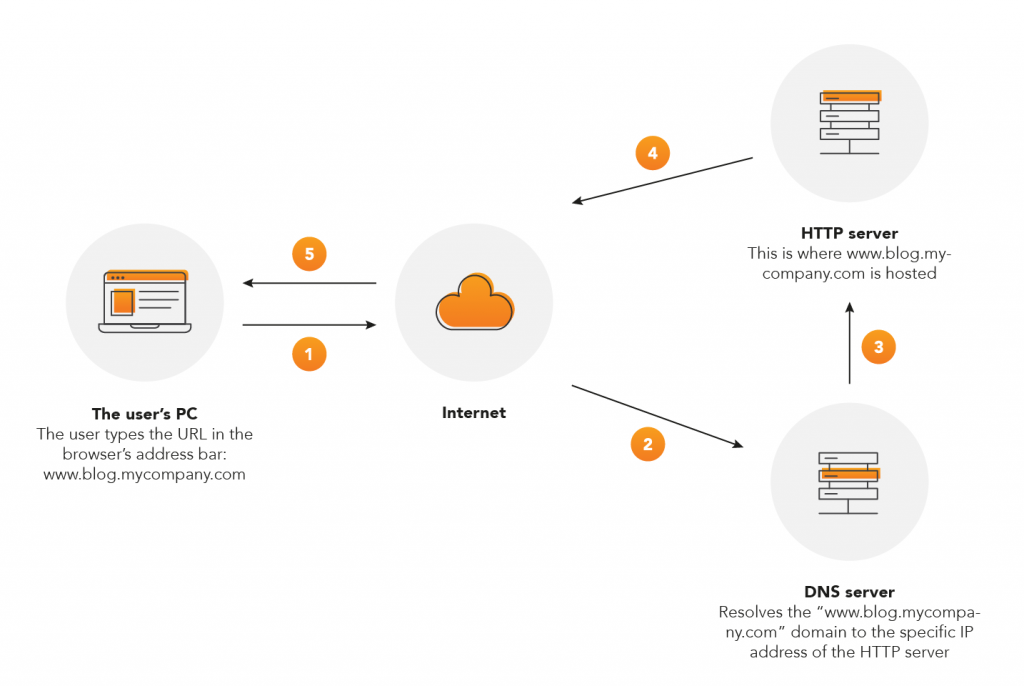
Once set up properly, your WordPress blog is ready to be populated with content and visited by your company’s prospective customers (in a manner similar to that shown in the above diagram). Unfortunately, there is also the other side of the coin, namely the potential attackers’ interest in your site.
Of course, this begs the question of how an attacker would know about a blog you have posted a few days ago. The answer is that every server publicly available on the Internet is scanned on a daily basis by various bots, or indexing scripts to be more precise (such as those used by online search engines). For example, there is a search engine available at www.shodan.io that looks for devices connected to the Internet, such as the server on which your blog is running. So, let’s see how many results will be returned for a simple query: “wordpress”.
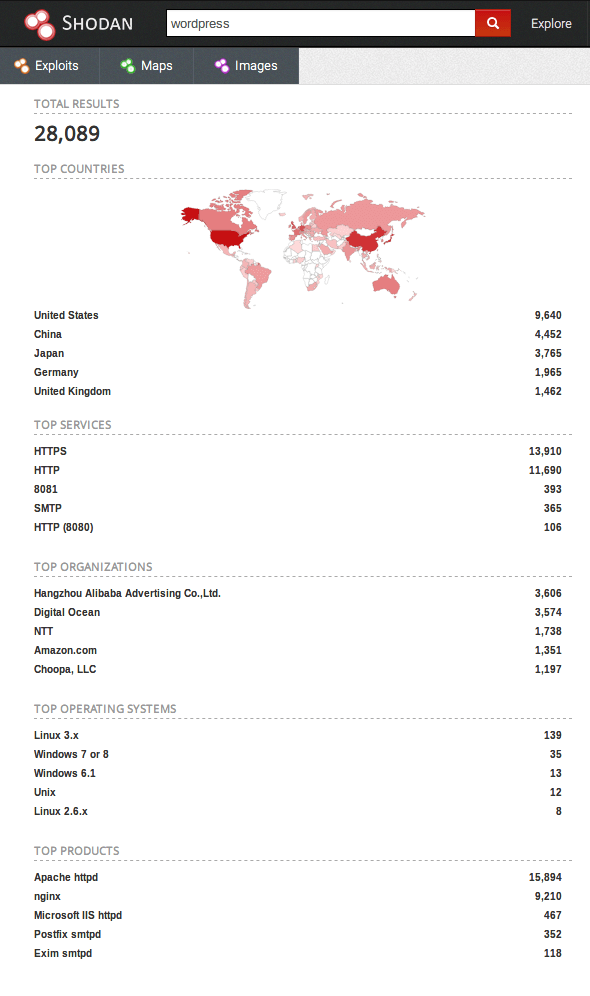
The sample query returned more than 28,000 results associated with the phrase “wordpress”. Obviously, this does not mean that there is a WordPress instance running on each of these devices or that there are only 28,089 such pages. 🙂
The Shodan.io search engine only looks for those publicly available devices that have (among other things) incorrectly implemented server or service configurations, known vulnerabilities or outdated software versions.
All this information can be useful to an attacker to some degree. The question is, what does the attacker stand to gain? Regardless of the type of information being posted on a blog, attackers’ typical motivations include:
- Using vulnerabilities in the installed software to take over the server and:
- Use the server’s resources for cryptocurrency mining.
- Create a botnet (a network of compromised computers) to carry out global attacks (e.g. DoS/DDoS attacks).
- Making a statement or trying to undermine the reputation of the page (depending on the blog’s popularity), which may include intentional malicious action by a frustrated user. 🙂
- Increasing the attacker’s security testing skills.
- Performing an act of unfair competition.
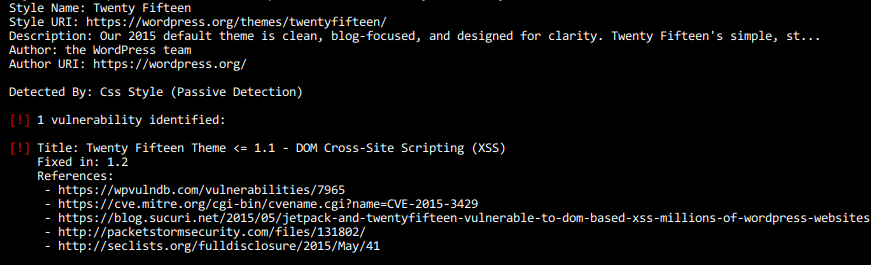
The attack vector may not necessarily be limited to the WordPress instance; it may also include themes or plugins installed on the platform and, above all, the infrastructure on which it is running. Off-the-shelf tools designed to test WordPress security are readily available and can pose a real threat even in the hands of an inexperienced attacker. To make things worse, some of these tools provide the user with step-by-step guidance. The figure below shows a snippet of the output generated by one of such programs. It contains information on the vulnerability discovered in the theme being used and provides links to sources of information on how the vulnerability can be exploited.
Now that you realize how easy it is to become exposed to an attack when keeping a blog, another question comes to mind…
How do you ensure the security of your WordPress blog?
I believe that WordPress is a relatively secure content management and delivery platform as long as you abide by some basic rules.
1. Update your software on a regular basis
WordPress releases very frequent updates which are really easy to install. In addition, it is a popular online platform, which is a good thing when new critical vulnerabilities appear that require installing a new update, because you will certainly learn about it quickly from popular sources on the Internet.
Besides WordPress itself, you also need to keep an eye on the infrastructure on which your WordPress instance is running, including the HTTP server, SQL database, operating system, etc., since all these components require regular updates.
2. Use configurations that comply with good practices
A “good practice” configuration covers the services and software that enable you to run your WordPress site and make it accessible to users. Properly implemented settings improve not only the security, but also the performance of your site.
3. Create regular backups
Failures can happen to anyone and aren’t necessarily the result of a server administrator or platform error. Recovery from a failure can be very quick as long as regular backups are created. Another very important consideration is that backups should be stored in a different location than that in which WordPress is running.
4. Use encrypted HTTPS communication
The use of encrypted communication between the user’s browser and the website is a de facto standard on the Internet today. Encryption mainly protects the data in transit between the parties (e.g. mission-critical data), but it also helps build confidence in the site being visited. It is also worth noting that Google gives higher ranks to websites which provide HTTPS-encrypted communication.
5. Use secure logon functionality for the platform
Strong, unique user and admin passwords are one thing, but it is also worth considering the use of two-factor authentication. When you do that, it is no longer enough for the attacker to acquire your account password; they also need to have an authentication code, for example a code from Google Authenticator (this functionality is provided by a plugin with the same name).
6. Minimize the number of installed plugins and add-ons
The ability to contribute to WordPress’s development comes with a variety of side effects. While this is an excellent initiative that enables everyone to make their mark, some contributors are not professional developers. As a result, publicly available and free WordPress add-ons aren’t always written according to good practices, which means that they can become an attack vector due to poor or inexistent security.
This is why I share the view that the main problem with WordPress is not the platform itself, but rather the plugins that extend it. This has actually been confirmed by, for example, search engines that look for exploits, that is “ready-made” scripts designed to exploit specific vulnerabilities for a specific purpose. Most search results point to vulnerabilities associated with plugins and other add-ons, such as themes.
Therefore, my next recommendation as regards WordPress security is to minimize the number of installed add-ons, and to only use reputable plugins which have a high number of active installations and remain in active, regular development. The required information can be found next to each search result on the WordPress plugin search page. The example below shows the Akismet Anti-Spam plugin, which is designed to protect against unwanted spam comments.
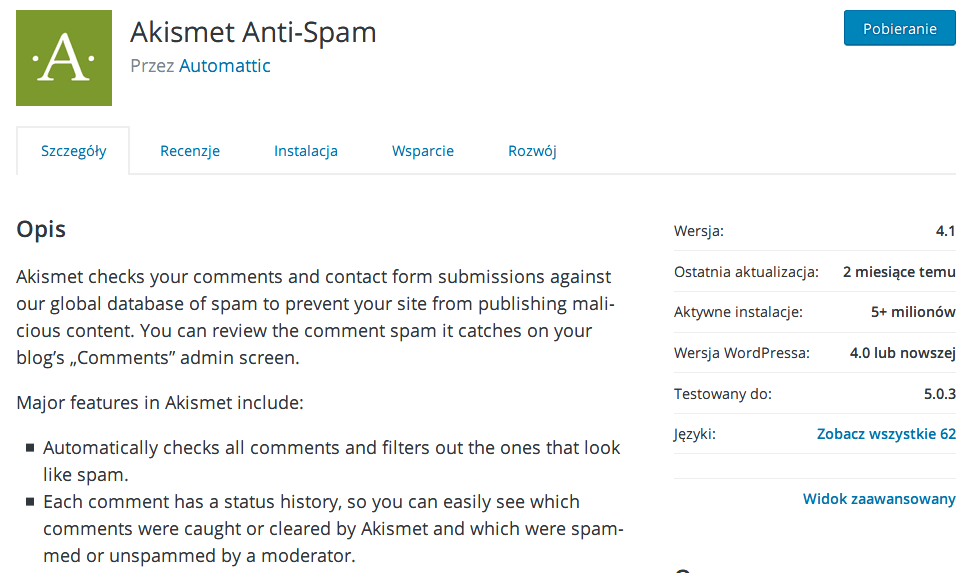
Naturally, you must also remember to update your installed plugins on a regular basis. Doing that from WordPress is very simple and takes just two or three clicks as shown in the figure below.
7. Use additional security-enhancing solutions
You can take advantage of solutions that support the operation of your website by improving infrastructure performance and offering protection against threats such as DoS/DDoS attacks, or by running automated application security scans.
Such services are provided, for example, by Cloudflare and can also be used for WordPress-based sites.
8. Regularly secure your infrastructure
Your infrastructure comprises a number of solutions which rely on administrator-defined configurations. It is absolutely crucial that these configurations are correct and consistent with the good practices I mentioned earlier, which is why you need to validate them on a regular basis and adapt them to the rapidly changing requirements.
This involves regular “hardening”, which is a series of activities intended to bring the security configuration of your services and software in line with specific guidelines or standards.
9. Conduct WordPress security audits or penetration tests
If the WordPress blog or page is critical to your business, consider having an audit or penetration test conducted by a third-party provider. The resulting audit or test report will make you aware of the actual security level and provide appropriate recommendations.
How can Onwelo help?
Here at Onwelo, we are fully aware that keeping the infrastructure secure is one of the main foundations of a prosperous business. This is why we frequently respond to the needs of our clients by offering audit and penetration testing support for Web applications (including those based on WordPress) and by helping secure such applications against threats.
Please contact us if you are interested in these or similar services! 🙂
By Grzegorz Wróbel – online (and not just online) security enthusiast. At Onwelo, he is responsible for security audits and penetration tests; after work, he constantly expands his expertise in this field. In his free time, he hones his DevOps skills, collects old and venerable computer hardware and listens to classic rock.
Leave a Reply
Recommended
From reconnaissance to reporting – about the security testing process
Penetration testing (or pentesting) is an authorized process of finding weaknesses, vulnerabilities and security risks, in order to prevent them from being exploited by potential adversaries. We will go through the basic methodology and more technical (and non-technical) details of the penetration testing process.
Phishing campaign – simulated attack on an organization as an effective way to fight cybercrime
Hacking attacks are on the rise. In the era of the pandemic, there has been a large increase in phishing campaigns thematically related to COVID-19.
Business continuity in times of crisis and RPA technology
The COVID-19 pandemic has created a crisis the size and scope of which no one could have previously imagined. What is more, it is more severe than most crises before – it has led to a revolution on an unprecedented scale, bringing almost the entire business world to a standstill and creating quite a challenge for organizations.
From reconnaissance to reporting – about the security testing process
Penetration testing (or pentesting) is an authorized process of finding weaknesses, vulnerabilities and security risks, in order to prevent them from being exploited by potential adversaries. We will go through the basic methodology and more technical (and non-technical) details of the penetration testing process.
Phishing campaign – simulated attack on an organization as an effective way to fight cybercrime
Hacking attacks are on the rise. In the era of the pandemic, there has been a large increase in phishing campaigns thematically related to COVID-19.